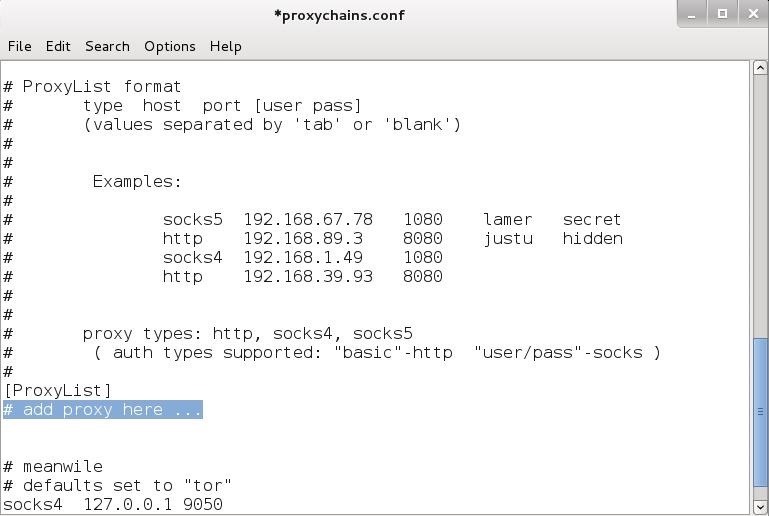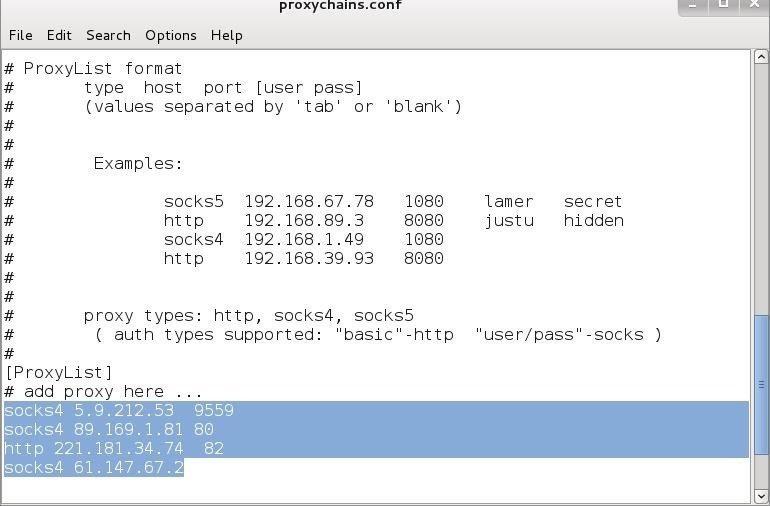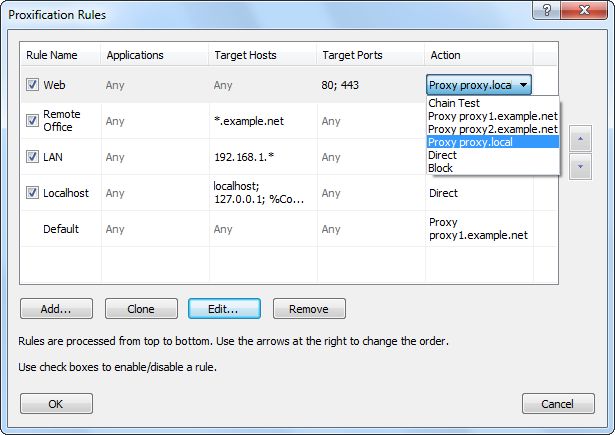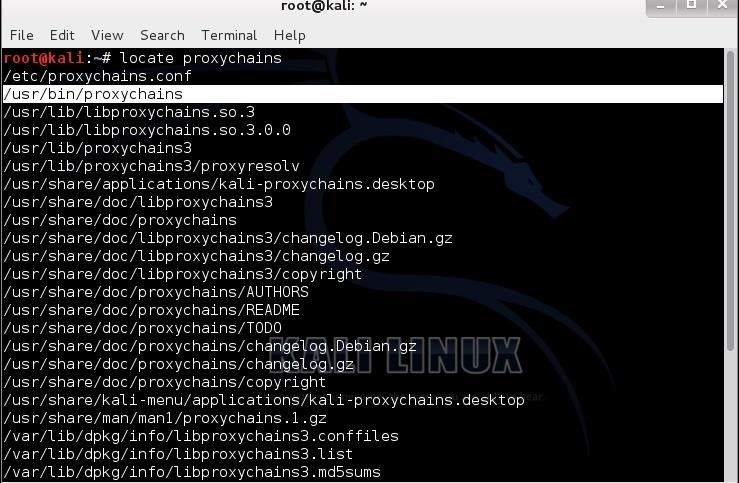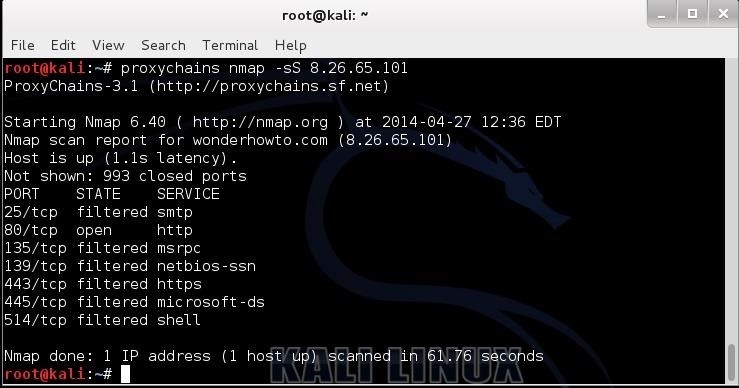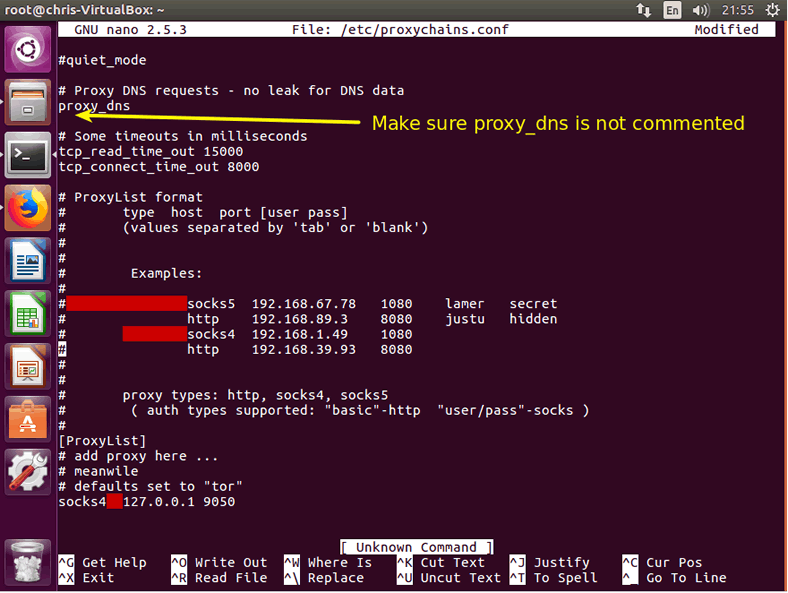
How to set proxychains with public or private proxies – Reviews & Discounts Codes | BestProxyProviders
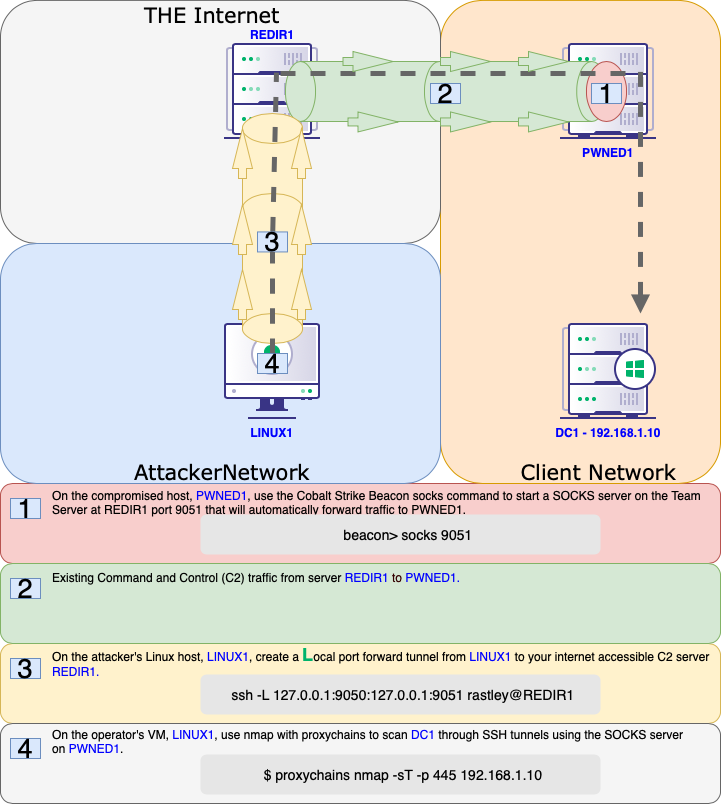
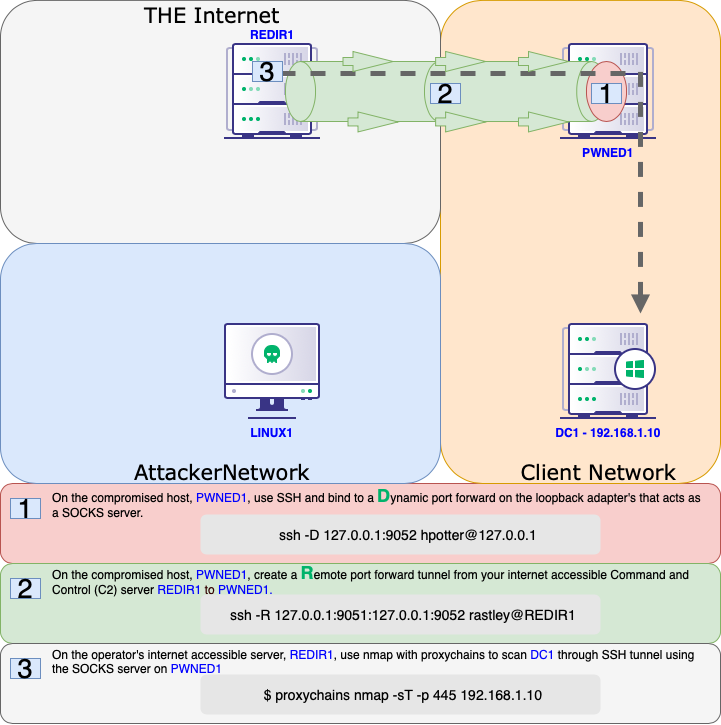
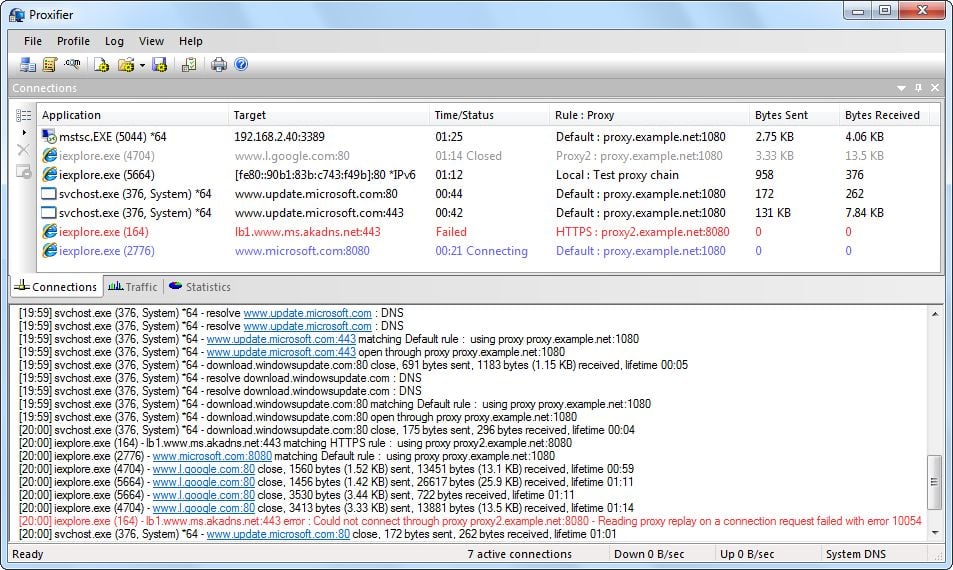
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members
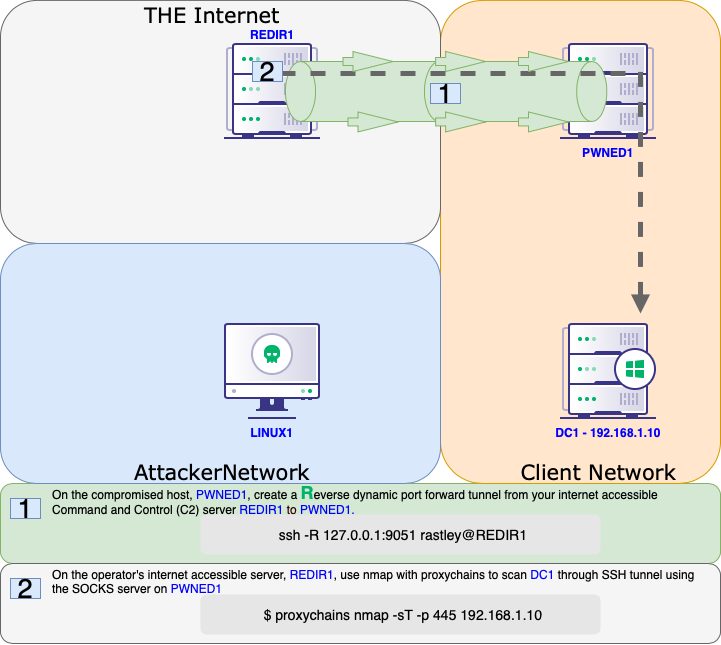
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members

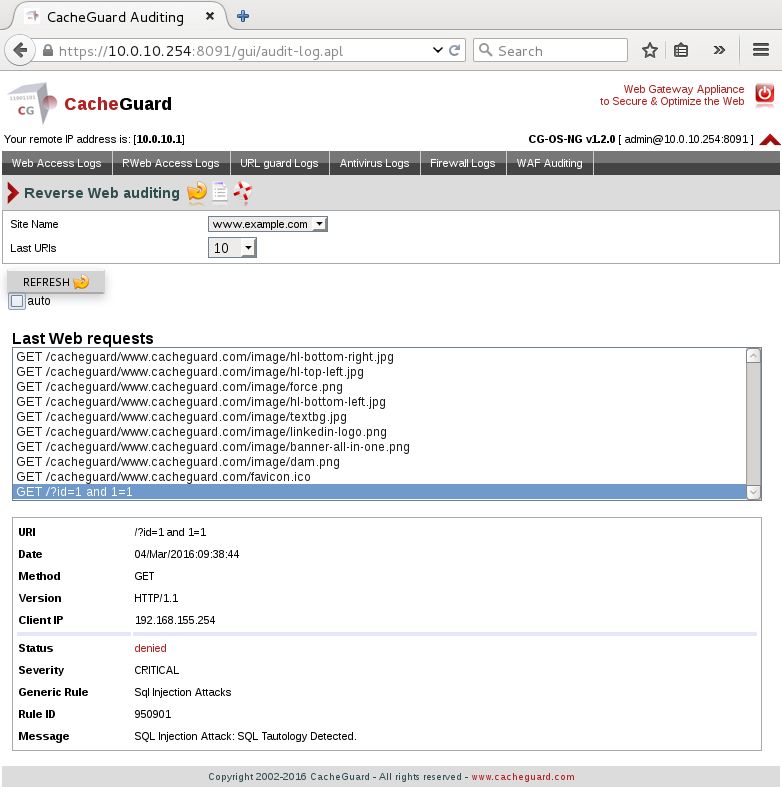
🔹How to Transparently Route Traffic Through Tor🔹 - Mindhack Diva-Cyber Security Knowledge and Wisdom - Medium