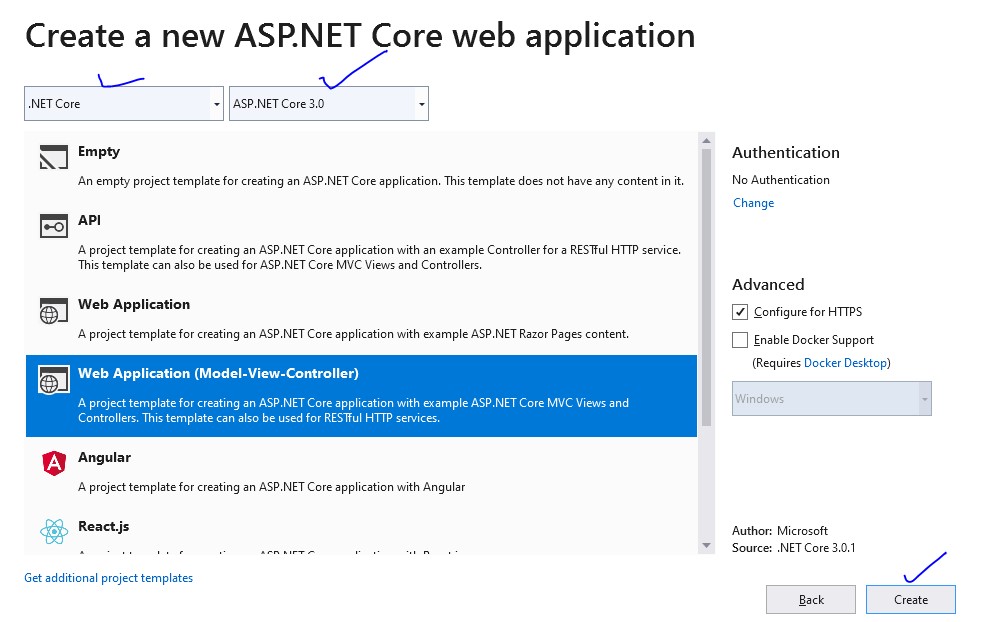
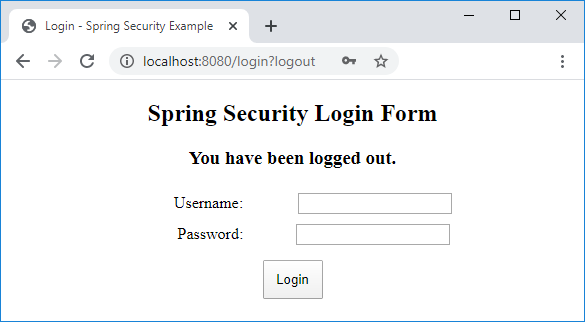
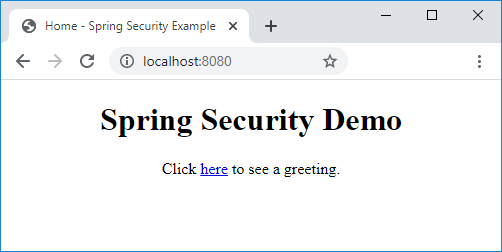
2. Spring Boot | Spring Security | Authentication | In Memory Authentication | BCrypt Encryption - YouTube

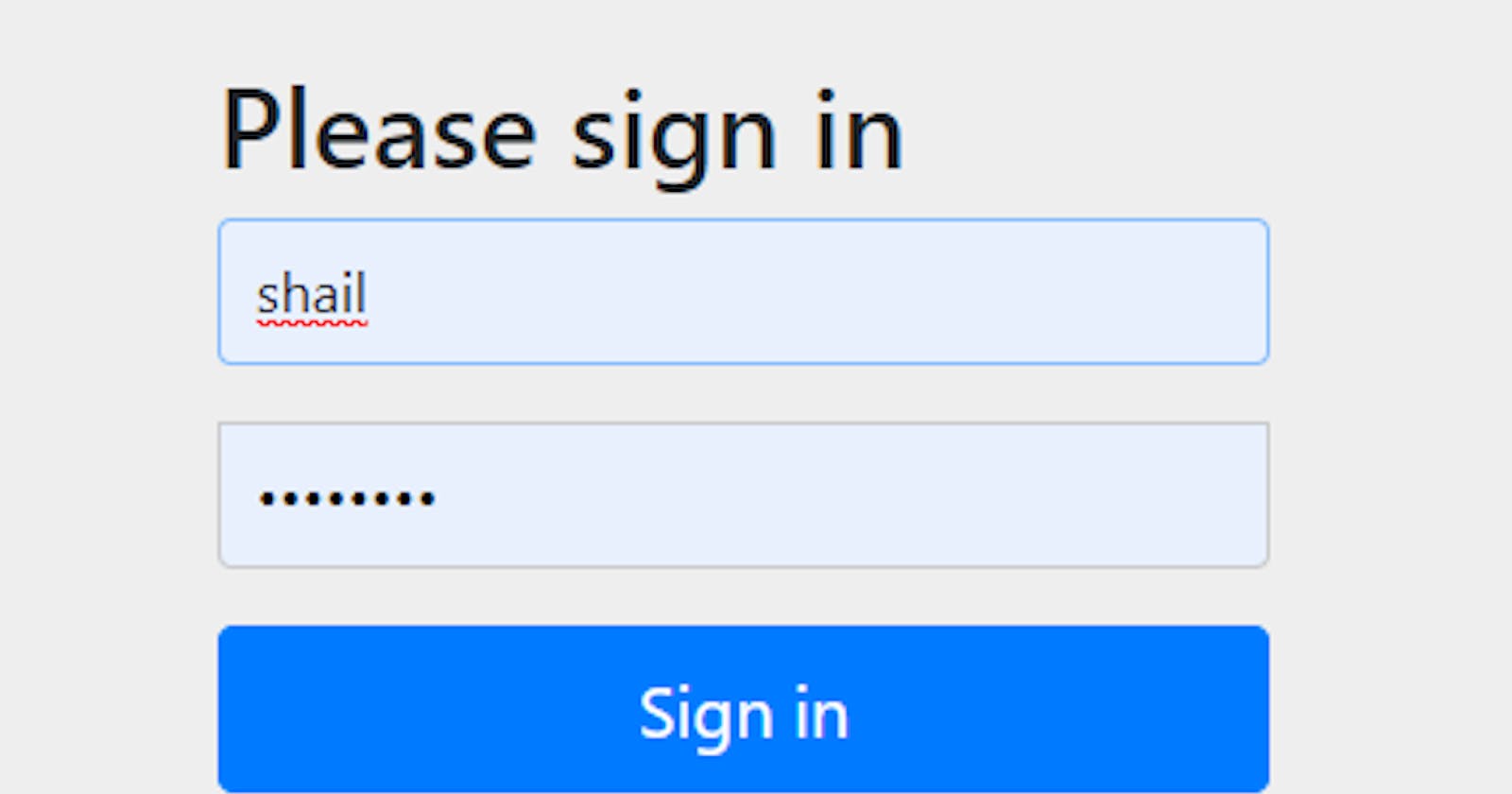
Spring Security + Thymeleaf — In memory User Details Configuration (Spring Security — 1) | by Amila Iroshan | The Fresh Writes | Medium