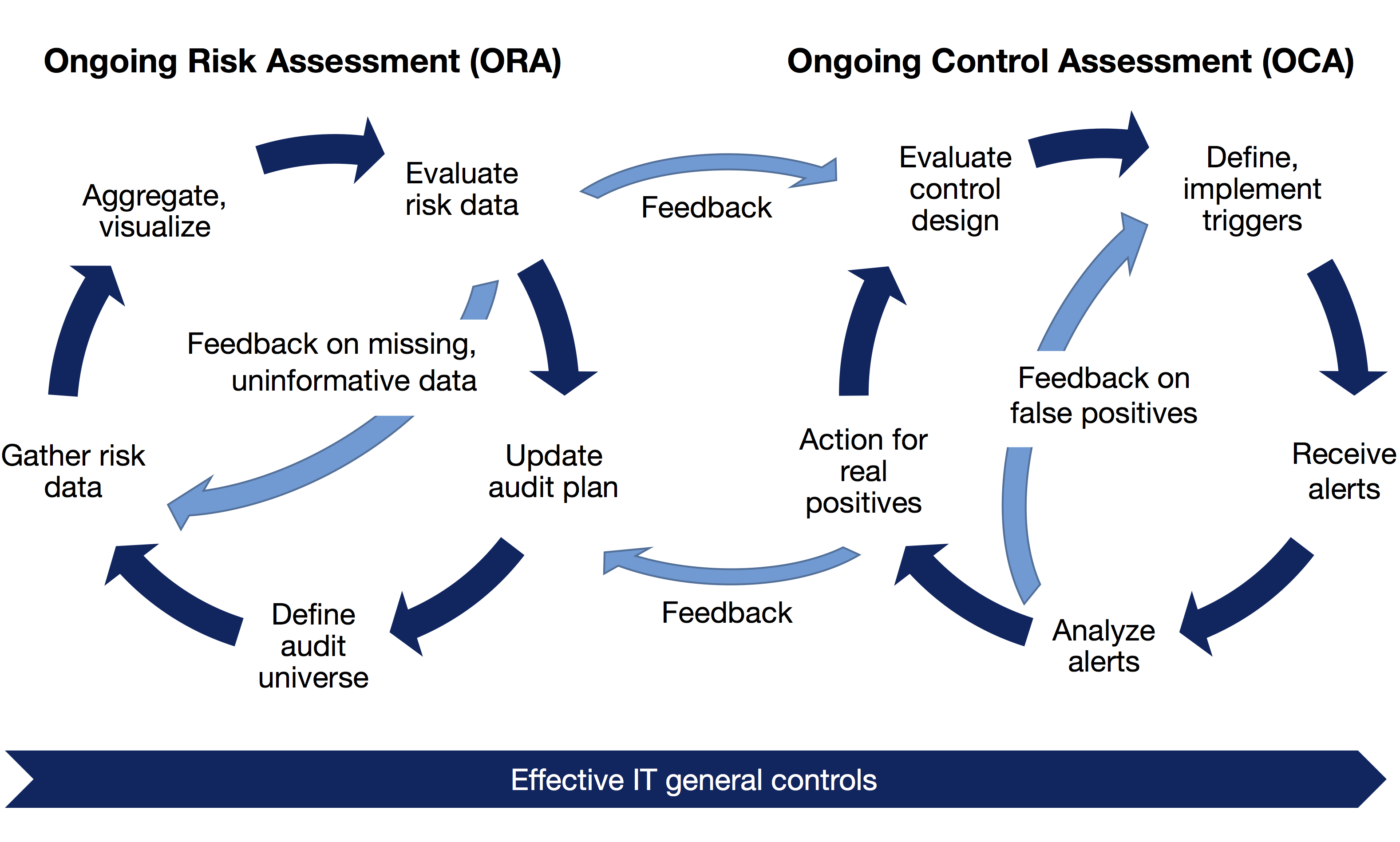
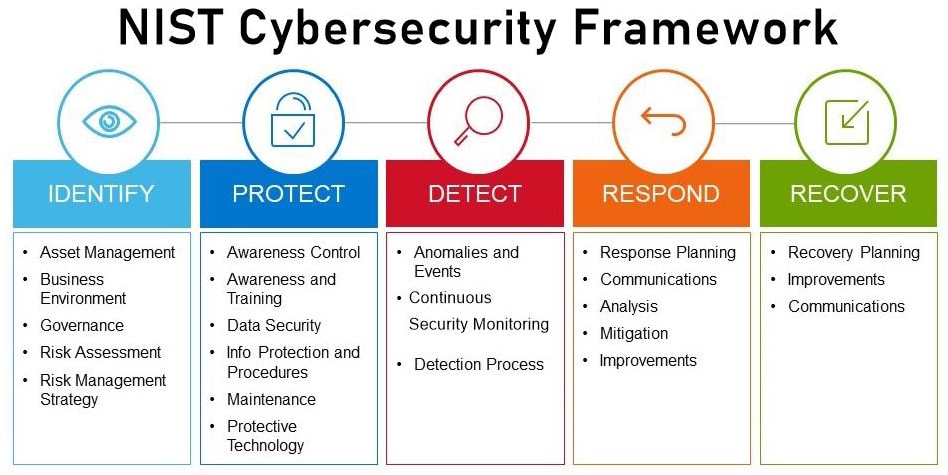
Bottomline Technologies on Twitter: "Definitive word from @Gartner_inc on #financial #fraud prevention: continuous #risk assessment a must. https://t.co/V3JeyBef1H #Sibos https://t.co/zYSR2TpSNC" / Twitter
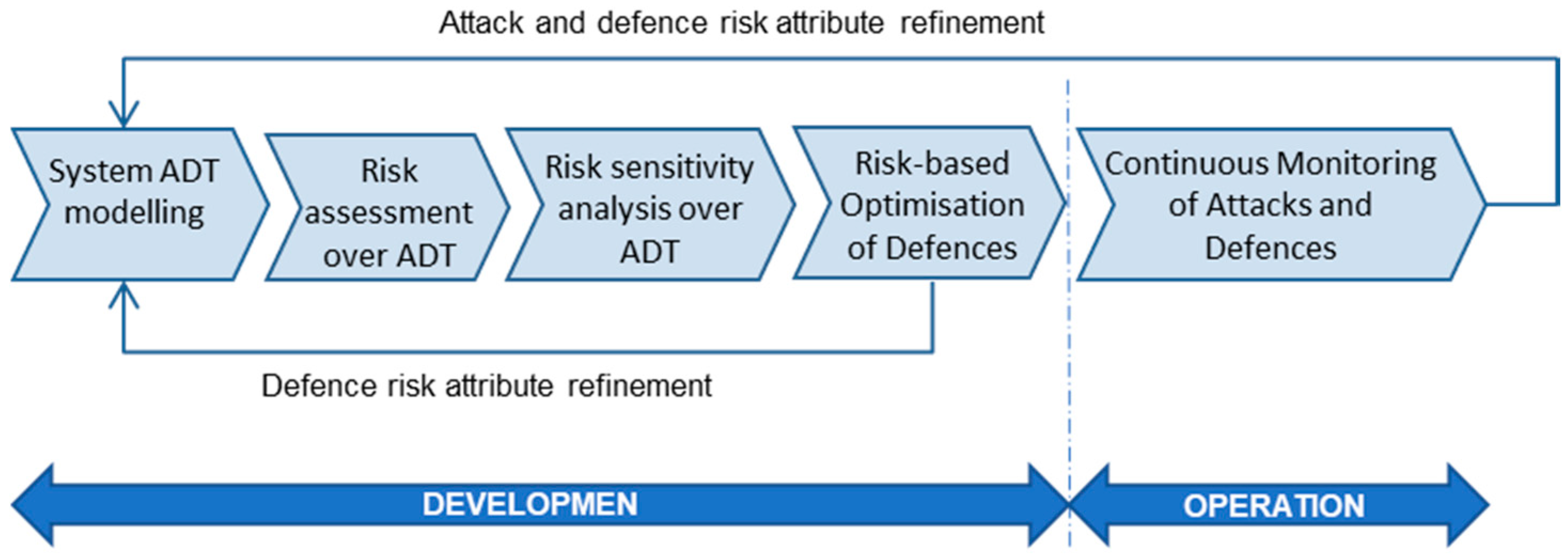
Sensors | Free Full-Text | Continuous Quantitative Risk Management in Smart Grids Using Attack Defense Trees



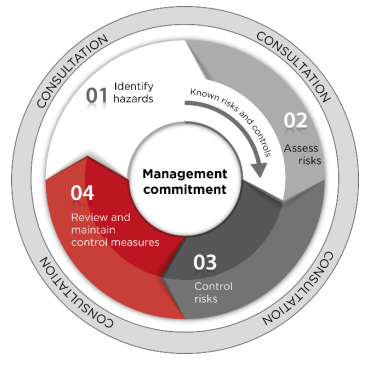
![CONTINUOUS PROCESS FOR RISK ASSESSMENT [3] | Download Scientific Diagram CONTINUOUS PROCESS FOR RISK ASSESSMENT [3] | Download Scientific Diagram](https://www.researchgate.net/publication/258513152/figure/fig1/AS:392770847035393@1470655275230/CONTINUOUS-PROCESS-FOR-RISK-ASSESSMENT-3.png)